Cyber attacks & cyber threats: types and prevention
In today’s digital era, where most of our personal and professional activities take place online, cyber attacks have become a serious threat to individuals, businesses and government institutions. Cybersecurity is therefore a key area dealing with the protection of systems, networks and data from unwanted attacks. Understanding what a cyber-attack is, how it takes place and what its most common forms are, is the first step towards being able to counter and effectively protect against these threats. This article will introduce you to the different types of cyber attacks and explain how they work.

In the article you will learn:
Cyber attack definition
Cyber attacks are attempts to steal, alter, destroy, disrupt or render inoperable information resources and systems in computer networks and systems. Cyber attacks can be classified into two categories: internal threats or external threats. Internal threats result from individuals with legitimate access to the systems they target exploiting their access to intentionally or unintentionally exploit vulnerabilities.
They can be carried out by a disgruntled or angry employee or contractor with access to the organisation’s systems. An external threat comes from someone who has no relationship to the system being attacked, such as a criminal organisation or hackers.
Cyber attacks can target a wide range of victims, from individual users to businesses or even governments. In attacks on businesses or other organisations, the hacker’s goal is usually to gain access to sensitive and valuable company resources, such as intellectual property, customer data or payment data.
How does a cyber attack start?
A cyber attack starts with the attacker choosing a target, which can be an individual, an organization or a specific vulnerability, such as outdated software or weak security configurations. Attackers gather information about the target through techniques such as scanning networks, searching for exposed systems, or even mining data publicly available online. Once they have enough information, they exploit system weaknesses to gain unauthorized access.
How does a cyber attack work?
- Initial access: the attacker establishes a position in the system, often by exploiting vulnerabilities or using social engineering methods such as phishing to trick users into giving up their data. This can also include brute force attacks on weak passwords or the use of stolen credentials from previous data breaches.
- Execution: after infiltrating the system, the attacker can execute malicious code that is often disguised as legitimate software or embedded in files such as email attachments. The code usually connects to the attacker’s server and downloads additional tools or instructions.
- Higher privileges: the attacker attempts to gain higher privileges on the system, such as administrator access, in order to move freely and perform more advanced operations. Often this involves exploiting system vulnerabilities or misconfigurations.
- Expanding the attack: after gaining access to a single system, the attacker moves laterally across the network, attempting to gain control of multiple devices and access to sensitive areas such as databases or domain controllers. Often, they reuse credentials or exploits other vulnerabilities to spread.
- The ultimate goal: the attacker can steal data, install ransomware to encrypt files and demand payment, disrupt traffic, or sabotage the network. In some cases, the attacker remains hidden for an extended period of time (Advanced Persistent Threat / APT) and continues to extract valuable data.
Throughout the whole process, attackers use a variety of techniques to avoid detection, such as encryption, obfuscation or log deletion. Cyber attacks can vary in complexity, but often follow this general pattern:
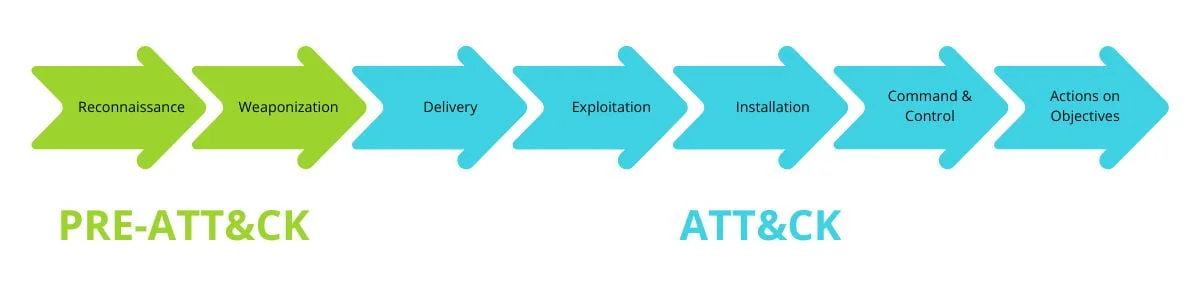
Cyber attack types
There are many types of cyber-attacks occurring in the world today. Knowing the different types of these attacks makes it easier for us to protect our networks and systems from them. In this section, we will take a closer look at the most commonly occurring cyberattacks that can affect an individual or a large company, depending on the scale.
1. Malware definition
Many people don’t know the answer to the question of what malware is. They have met it, heard about it, but they don’t know how to define it. Malware is any type of software designed to damage, misuse or gain unauthorised access to computers, networks or devices. It is used by cybercriminals to steal sensitive data, disrupt operations or take control of systems for malicious purposes.
Malware can enter your system through fraudulent emails, malicious downloads, infected websites or compromised software updates. Once inside the system, it can perform a variety of malicious activities, such as stealing data, spying on users or corrupting files.
Malware types
- Rootkit attack – unlike other malicious codes, a rootkit is a set of software tools that are used to open a “back door” in the victim’s device. This allows the attacker to install additional malware, such as ransomware and keyloggers, or gain remote access and to take control over other devices on the network. To avoid detection, rootkits often disable security software. Once a rootkit gains control of a device, it can be used to send spam, join a botnet, or collect sensitive data and send it back to the attacker.
- Trojan horse (Trojan virus) – a Trojan horse is a program downloaded and installed on your computer that appears to be harmless, but is actually malicious. Usually this malware is hidden in an innocent-looking email attachment or a free downloaded application. When the user clicks on the attachment or downloads the program, the malware is transferred to their computing device. Once inserted, the malicious code will perform whatever task the attacker has designed. Often this is to launch an immediate attack, but it can also create a backdoor that the hacker will use in future attacks.
- Spyware virus – once installed, spyware monitors the victim’s Internet activity, tracks login credentials, and spies on sensitive information – all without the user’s consent or knowledge. For example, cybercriminals use spyware to obtain credit card and bank account numbers and to obtain passwords. Government agencies in many countries also use spyware – most famously a program called Pegasus – to spy on activists, politicians, diplomats, bloggers, research labs and allies.
- Ransomware cyber attack – ransomware is a type of malware that blocks access to files or an entire system by encrypting them. After blocking access, the aggressors demand a ransom to decrypt them. This type of attack is usually very fast and can also affect backups, making it difficult to restore systems without paying a ransom. Ransomware is often spread through phishing emails or infected websites. A famous example is the WannaCry ransomware attack, which affected thousands of organizations worldwide.
- Adware – adware is software that displays unsolicited advertisements on a user’s device, often without the user’s consent. Although adware may not always be malicious, it can disrupt the user experience by slowing down the device and displaying ads continuously. It is often installed unknowingly, for example alongside free software. In some cases, adware can track a user’s online behaviour to target ads or obtain sensitive data.
- Worms virus – worms are self-replicating malicious programs that spread over networks without the need for user interaction. Unlike viruses, worms do not need to bind to other programs or files. Their main goal is to infect as many devices as possible and spread as quickly as possible. Worms can cause serious damage, such as overwhelming networks, slowing down systems or installing more malware. An example is the Morris Worm, one of the first major Internet worms.
- Botnet – a botnet is a network of infected devices (called “bots”) that are under the control of an attacker. The devices in a botnet can be used for coordinated attacks, such as distributed denial of service (DDoS) attacks, in which the botnet overwhelms the target server with an excessive number of requests, thus taking it out of service. Devices can be infected with various types of malware, often without the user’s knowledge. Botnets are also used to spread spam or steal data.
2. Denial of service attack definition
A denial-of-service attack (DoS attack) is a malicious, targeted attack that floods a network with fake requests in order to disrupt business operations.
In a DoS attack, users cannot perform normal and necessary tasks, such as accessing email, websites, online accounts or other resources that are hosted by the compromised computer or network. Although most DoS attacks do not result in data loss and are usually resolved without paying a ransom, they do cost an organization time, money and other resources to restore critical business operations.
The difference between DoS and distributed denial of service (DDoS) attacks is related to the origin of the attack. DoS attacks originate from a single system, whereas DDoS attacks originate from multiple systems. DDoS attacks are faster and harder to block than DOS attacks because multiple systems must be identified and neutralized to stop the attack.
3. Phishing definition
Phishing is a cyber-attack in which an attacker attempts to extort sensitive information such as usernames, passwords, credit card numbers or other personal data from individuals. It is usually a fraudulent communication, often in the form of an email or text message that pretends to come from a legitimate source, such as a trusted company or colleague.
Phishing types
1. Email phishing
Email phishing is the most common type of phishing attack, in which aggressors send fraudulent emails en masse, pretending to come from trusted sources such as banks, online services or well-known companies.
- The email contains a malicious link or attachment that, when clicked, redirects the victim to a fake website that resembles a legitimate one. Victims are then tricked into entering personal information such as login or credit card details.
- Example: an email that looks like it’s from a bank and asks you to update your account details using the link provided.
2. Spear phishing
Spear phishing is a more targeted form of phishing aimed at specific individuals or organizations.
- Unlike mass phishing emails, spear phishing attacks use personalized information (such as the recipient’s name, job title or details of a company project) to make the message look more legitimate.
- Example: a spear phishing email may appear to come from a colleague or boss asking you to send sensitive company information or reset your password.
3. Whaling
Whaling focuses on high-ranking individuals within an organization, such as CEOs or senior executives.
- Aggressors pose as a trustworthy person, often using urgent business matters as a lure. These emails are highly personalised and target executive-level information such as business credentials, financial data or strategic plans.
- Example: an email to a CEO posing as a legal authority or other senior executive requesting sensitive business documents or large bank transfers.
4. Vishing (voice phishing)
Vishing includes phishing attacks conducted via phone calls.
- Aggressors pose as trusted organizations such as banks or government agencies and persuade victims to provide sensitive information such as passwords, bank details or social security numbers.
- Example: a phone call from your bank asking for your account number or PIN to “verify” your identity.
5. Smishing (SMS phishing)
Smishing is phishing via SMS or text messages.
- The attacker sends a text message containing a malicious message or phone number that urges the recipient to take urgent action. The goal is often to steal personal data or infect a mobile device with malware.
- Example: if an e-mail message appears on the Internet that is related to a mobile phone, it may contain, for example, a text message claiming that your bank account is blocked and asking you to click on a link to verify your account details.
4. Spoofing attack
The definition of a spoofing attack is simple. It is a type of cyber attack in which an attacker impersonates a trusted entity or system to deceive individuals or systems into granting access or sharing sensitive information. The main objective is to gain unauthorized access, steal data or launch further attacks under the guise of a legitimate source. Spoofing can occur in a variety of contexts, from email communications to network connections.
Spoofing types
1. E-mail spoofing
Aggressors send fraudulent emails pretending to come from a trusted sender, such as a colleague, business partner or a well-known company.
By changing the “From” field in the email header, they create the impression that the email is coming from someone else. This type of spoofing is often used in phishing attacks to trick the recipient into sharing sensitive data or clicking on malicious links.
Example: receiving an email that looks like it’s from your bank and asks you to log in or reset your password using a fraudulent link.
2. IP spoofing
Aggressors manipulate the source IP address in the packet header to make the packet appear to come from a trusted or known IP address.
IP spoofing is commonly used to gain unauthorized access to a network or to launch distributed denial of service (DDoS) attacks by flooding a target with traffic from many spoofed IP addresses.
Example: an attacker sends malicious data packets to a system that appear to come from a trusted source on the network.
3. URL spoofing
Attackers create fake websites to mimic legitimate websites, often with the aim of stealing sensitive information such as usernames, passwords or payment details.
An attacker registers a domain name similar to a trusted website, changing one or two characters to trick users (e.g., “g00gle.com” instead of “google.com”). When users visit the fake website, they are tricked into entering sensitive information.
Example: a fraudulent website that looks like an online banking login page but is actually controlled by an attacker to obtain login credentials.
4. ARP spoofing
An attacker sends spoofed ARP messages within the local network to associate its MAC address with the IP address of another device, often a gateway or router.
This type of attack allows an attacker to intercept, modify, or stop the transmission of data between devices on a network. It is often used in Man in the Middle (MITM) attacks.
Example: if an attack occurs on the network, it is possible that an attack that violates the rules that apply to the network will occur on the network: the attacker will intercept the communication between your device and the router, allowing him to monitor or modify the data that is sent and received.
5. Identity-based attacks definition
Identity-based attacks are very difficult to detect. If a user’s valid credentials have been compromised and an adversary is impersonating that user, it is often very difficult to distinguish typical user behaviour from that of a hacker using traditional security measures and tools.
Types of identity-based cyber attacks
1. Man in the middle attack (MITM)
A MITM attack occurs when an attacker secretly intercepts and potentially alters communications between two parties. The goal is often to steal sensitive data such as login credentials, banking information or personal details. The attacker inserts themselves between the victim and the target, often using techniques such as Wi-Fi eavesdropping or DNS spoofing. The attacker can simply listen in on or modify a conversation, redirect funds, convince the victim to change passwords, or perform unauthorized actions.
Example: capturing communication between a user and their bank during an online transaction.
2. Pass-the-hash attack
In a Pass-the-Hash (PtH) attack, cybercriminals steal a hashed version of the password, which is an encrypted representation of the original password. Instead of cracking the password, the aggressors use the hash directly to authenticate and start a new session. This attack is common in Windows environments where the hash is stored and transmitted over the network.
Example: an attacker gains unauthorized access to a corporate network by using a stolen hash from an attacked device without cracking the actual password.
3. Golden ticket attack
The Golden Ticket attack involves exploiting vulnerabilities in the Kerberos authentication protocol used by Microsoft Active Directory. Aggressors create a “golden ticket” that gives them unrestricted access to the domain controller and other critical resources on the network. By using the golden ticket, aggressors can bypass authentication and retain persistent access.
Example: an attacker steals key data from a domain controller and creates a golden ticket that allows unrestricted access to the organization’s entire network without the need for re-authentication.
4. Silver ticket attack
Silver ticket attack is similar to golden ticket attack but has a more limited scope. Aggressors create fake service tickets to gain access to specific services. After stealing the password to an account with service-level access, the attacker creates a fake authentication ticket that provides unauthorized access to a specific service (e.g., file shares, databases) on the network.
Example: gaining access to a specific application server by forging a service ticket using a stolen password.
5. Credential harvesting
Credential harvesting refers to the collection of user credentials, including usernames, passwords and other login credentials, often through phishing, keylogging or intrusion. Attackers collect this information in order to use it for unauthorized access or to sell it on the dark web. Login credentials are often collected in bulk from a variety of sources, including phishing websites or malware infections.
Example: a phishing email tricks the victim into entering their login details on a fake website, which the attackers then use to gain access to their real accounts.
6. Credential stuffing
Credential misuse involves using stolen credentials from one compromised system to attempt to access other systems. Since people often reuse passwords across multiple accounts, aggressors attempt to log into unrelated services (such as email, social networking, or banking) using credentials obtained from other breaches.
Example: using credentials stolen from a compromised e-commerce website to attempt to access a victim’s social media accounts.
7. Password spraying
An attacker attempts to gain access to many accounts using one or more common passwords, thus avoiding being blocked. Unlike traditional brute force attacks, which target a single account with many passwords, a password hashing attack targets many accounts with several common passwords (e.g. “password123”). This helps avoid detection mechanisms that lock accounts after multiple failed login attempts.
Example: an attacker tries the password “Welcome2023” on hundreds of user accounts within an organization.
8. Brute force attacks
A brute force attack involves systematically guessing passwords or encryption keys by trial and error until the correct password is found. Aggressors use automated software to quickly try different combinations of usernames and passwords. If they have enough time and computing power, they can eventually find the right combination.
Example: an attacker uses a tool that, after trying thousands of combinations, guesses the correct password for an administrator account.
6. Code injection attacks
Code injection attacks involve an attacker inserting malicious code into a vulnerable computer or network to alter its course. There are several types of code injection attacks:
1. SQL injection
The SQL Injection attack exploits system vulnerabilities to inject malicious SQL statements into a data-driven application, which then allows a hacker to extract information from the database. Hackers use SQL Injection techniques to alter, steal, or delete data from an application’s database.
Imagine a website with a sign-up form. Normally, the application would send an SQL query to the database in the form:
SELECT * FROM users WHERE username = ‘user’ AND password = ‘password’;
However, if an attacker enters the following string in the username field:
‘ OR ‘1’=’1′
The SQL query could look like this:
SELECT * FROM users WHERE username = ” OR ‘1’=’1′ AND password = ‘password’;
This query is now always true because ‘1’=’1′ is a condition that is always satisfied. The attacker can log into the system this way without knowing the actual login credentials.
2. Cross-site scripting (XSS)
Cross Site Scripting (XSS) is a code injection attack in which an attacker inserts malicious code into a legitimate website. The code is then executed as an infected script in the user’s web browser, allowing the attacker to steal sensitive information or impersonate the user.
Web forums, discussion boards, blogs and other websites that allow users to post their own content are the most susceptible to XSS attacks.
3. Malvertising
The attack usually starts by breaking a third-party server, allowing the cybercriminal to insert malicious code into the ad being displayed or into an element of the ad, such as banner ad copy, a creative image or video content. When a website visitor clicks through, the corrupted code in the ad installs malware or adware on the user’s computer.
4. Data poisoning
Data poisoning is a type of cyber attack in which an adversary intentionally compromises a training dataset used by an artificial intelligence or machine learning model in order to manipulate the operation of that model. When manipulating the dataset in the training phase, the adversary may introduce bias, intentionally create incorrect outputs, introduce vulnerabilities, or otherwise affect the predictive capabilities of the model.
7. Supply chain attack
A supply chain attack is a type of cyber attack that targets a trusted third-party vendor that offers services or software critical to the supply chain. Software supply chain attacks inject malicious code into an application to infect all users of the application, while hardware supply chain attacks compromise physical components with the same goal.
Software supply chains are particularly vulnerable because modern software is not written from scratch: rather, it includes many off-the-shelf components such as third-party APIs, open source and proprietary code from software vendors.
8. Social engineering cyber attack definition
Social engineering is a technique in which attackers use psychological tactics to manipulate people into performing a desired action. Using powerful motivators such as love, money, fear and status, they can obtain sensitive information that they can later use either to blackmail an organization or to use this information to gain a competitive advantage.
Social engineering attack types
1. Pretexting
In pretexting, aggressors gain access to information, a system, or a user by faking a false scenario to gain the victim’s trust. This includes impersonating an investment banker, a human resources employee or even an IT specialist.
2. Business email compromise (BEC)
In a BEC attack, attackers assume the identity of a trusted user to, among other things, trick a company’s employees or customers into making payments or sharing data.
3. Disinformation campaign
Disinformation campaigns are deliberate efforts to spread false information, especially for political or war-related reasons. Adversaries use social media networks, which reach huge audiences, to spread false narratives through the prolific use of bots and fake accounts, creating a false sense of common opinion.
4. Honeytrap
Honeytrap attacks target people looking for love or friendship on dating apps/websites. Attackers create fake profiles and use the timelessly built relationship to trick the victim into giving them money, information or network access to install malware.
5. Tailgating/Piggybacking
Tailgating, also known as piggybacking, is a type of attack that is carried out in person by having the attacker stick close to an employee of the company and asking them to hold the door for them. Once inside the facility, the adversary attempts to physically steal or destroy sensitive information.
9. Insider threats definition
IT teams that focus solely on external threats are only addressing part of the security environment. Internal threats involving current or former employees pose a significant risk because these individuals have direct access to the company’s network, sensitive data, intellectual property, and often have valuable knowledge of business processes and policies that could facilitate an attack.
Although many insider threats are malicious and motivated by, for example, financial gain from selling confidential information on the dark web or emotional manipulation through social engineering tactics, not all are intentionally malicious. Some are the result of negligence.
To effectively address both malicious and reckless insider threats, organizations should implement a robust cybersecurity training program. This training should educate employees on recognizing and mitigating potential security risks, including those posed by insiders.
10. DNS tunneling definition
What is DNS tunneling ? DNS tunneling is a type of cyber-attack that uses Domain Name System (DNS) queries and responses to bypass traditional security measures and transfer data and code across a network.
Once infected, the hacker is free to perform command and control activities. This tunnel provides an avenue for the hacker to launch malware and/or obtain data, IP or other sensitive information by encoding it bit by bit in a series of DNS responses.
DNS tunneling attacks have proliferated in recent years, in part because they are relatively easy to deploy. Tunneling toolkits and tutorials are even readily available online through mainstream sites such as YouTube.
11. IoT-based attacks
An Internet of Things (IoT) based attack is any cyber attack that targets an IoT device or network. Once compromised, a hacker can take control of a device, steal data, or join a group of infected devices to create a botnet to launch DoS or DDoS attacks.
With the number of connected devices expected to grow rapidly, cybersecurity experts expect IoT infections to grow as well. In addition, the deployment of 5G networks, which will encourage the use of connected devices, may also lead to an increase in attacks.
12. AI-powered attacks
As AI and ML technologies improve, the number of use cases is also increasing. Just as cybersecurity professionals use AI and ML to protect their online environments, attackers are using these tools to gain access to networks or steal sensitive information.
Adversial AI/ML
Adversarial AI/ML attacks aim to disrupt or manipulate AI and machine learning systems by introducing misleading or inaccurate data during the training phase. By carefully crafting inputs that exploit model weaknesses, attackers can cause artificial intelligence to make incorrect predictions or decisions.
Example: imagine an autonomous vehicle powered by artificial intelligence that uses machine learning to recognise traffic signs and make driving decisions based on them. An attacker could use adversarial techniques to subtly change the appearance of a stop sign so that it appears to the vehicle’s AI system as a Yield Right of Way sign.
These changes could be imperceptible to human eyes, but would cause the sign to be misinterpreted by artificial intelligence, potentially leading to dangerous driving behaviour.
Dark artificial intelligence (Dark AI)
Dark AI refers to the malicious use of AI and ML technologies designed to exploit system vulnerabilities. Unlike conventional attacks, Dark AI often operates covertly, making it difficult to detect until significant damage is done. It uses advanced AI techniques to carry out sophisticated and covert attacks.
Example: the use of AI-driven tools to automatically discover and exploit security vulnerabilities in software or systems.
Deepfake
Deepfake involves the use of artificial intelligence to create highly realistic but fake media, including images, videos and audio. These fakes can deceive viewers by making it appear as if people said or did things they never did. Deepfakes can be used to manipulate public opinion, damage reputations or interfere in political processes.
Example: a doctored video of a political figure who made controversial statements that never actually happened.
AI-generated social engineering
Social engineering attacks generated by artificial intelligence include the creation of sophisticated chatbots or virtual assistants that mimic human-like interactions. These AI systems engage in conversations with users to obtain sensitive information or persuade them to take malicious actions.
Example: a persuasive chatbot with artificial intelligence posing as customer service asking users to provide personal information or login credentials.
How can a cyber attack be prevented?
Cyber attacks will become more frequent and sophisticated. The good news is that there are several things organizations can do to minimize the risk.
Update your software
Updated software systems are more resilient than outdated versions, which may have weaknesses. Updates can fix all bugs and weaknesses in the software, so it is optimal to have the latest version. In addition, consider updating your software by investing in patch management.
Install a firewall
Firewalls are useful in preventing various attacks such as DoS attacks. They work by controlling the network traffic that passes through the system. A firewall also stops any suspicious activity that it deems potentially harmful to the computer.
Back up your data
When you back up your data, you move it to a different, secure storage location. This could be using cloud storage or a physical device such as a hard drive. In the event of an attack, backing up your data allows you to recover any lost data.
Data encryption
Data encryption is a popular method of preventing cyber-attacks and ensures that data is only accessible to those who have the decryption key. To successfully attack encrypted data, aggressors often have to rely on the brute force method, where they try different keys until they guess the right one, which makes breaking encryption difficult.

Use strong passwords
To prevent attacks, you should have strong passwords in the first place and avoid using the same passwords for different accounts and systems. Repeated use of the same password increases the risk of aggressors gaining access to all your information. Updating your passwords regularly and using passwords that combine special characters, upper and lower case letters and numbers can help protect all your accounts.
Use two-factor authentication
Use two-factor or multi-factor authentication. Two-factor authentication requires users to provide two different authentication factors for their authentication. When more than one additional authentication method is required in addition to your username and password, this is referred to as multi-factor authentication. This turns out to be an important step to secure any account.
Participate in comprehensive cyber security training
Comprehensive cyber security training is one of the most effective ways to gain practical knowledge and skills to protect yourself and your business from cyber attacks. Such training provides participants with an in-depth understanding of the different types of threats and techniques to compromise systems and obtain sensitive data. In addition, participants will learn practical methods to detect, prevent, and respond to these attacks.
Conclusion on cyber attacks
In a digital age where we increasingly rely on technology, protecting against cyber attacks is an essential part of every organisation and individual. Cyber threats such as malware, ransomware, phishing and man-in-the-middle attacks are becoming increasingly sophisticated, causing serious financial and reputational damage.
Therefore, it is critical to have a robust cybersecurity strategy in place that includes not only technical measures, but also thorough user and employee education.
Properly securing data, monitoring activity on the dark web or investing in elite threat scanning services are just some of the key steps organisations can take. Regular cybersecurity training is also essential to minimize the risks of human error.
